Protect Your Code
Stop Malicious Packages
AI powered Human verified malicious package
protection working 24x7 for your developers
Your stack is full of moving parts.
We scan them all.
Built for the New Reality of Open Source
SafeDep protects developers from malicious code hidden in open source packages installed every day, guarding the entry point, not just the code inside.
Guard External Code Continuously
SafeDep addresses the real starting point of risk — third-party open source packages — by stopping malicious code before it ever reaches your repository.
Invisible in Developer Workflow
SafeDep runs inside your terminal and CI/CD pipeline. No extra dashboards. No context switching. Security that operates silently in the background.
Trust Through Transparency
SafeDep is open source by default, with no vendor lock-in. Developers see exactly what we scan and the reasons behind every blocked package.
SafeDep Watches
Every OSS Release
Every new package from npm, PyPI, RubyGems, and more is instantly scanned by SafeDep's AI-powered static code analysis engine to detect malicious intent before it spreads. The results are correlated with dynamic analysis in a sandbox and AI agents to ensure accuracy and context.
Scanning Dependencies
As You Code
We scan every dependency inside your pull requests and builds as they run. We block compromised packages before merge, keeping your codebase safe from hidden attacks
Generate Reports
You can Trust
SafeDep instantly stops malicious packages from entering your workflow, keeping your codebase safe long before public advisories are issued.
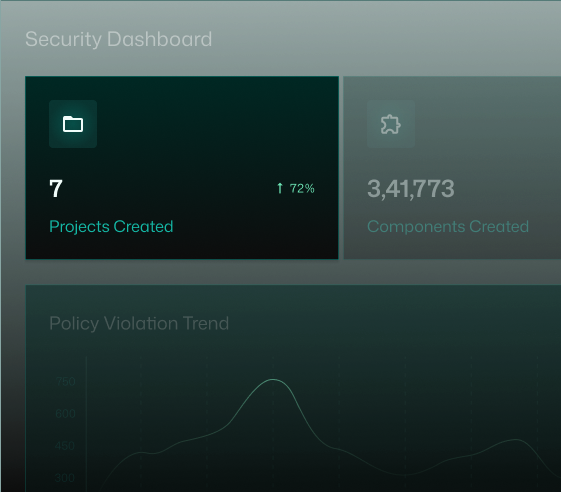
Govern and
Track Your OSS Security
Monitor every detected risk, enforce organization-wide policies, and generate audit-ready reports to prove your OSS supply chain is secure.
Your Security Command Center for Open Source.
Real-time visibility, policy control, and actionable intelligence, all in one view.
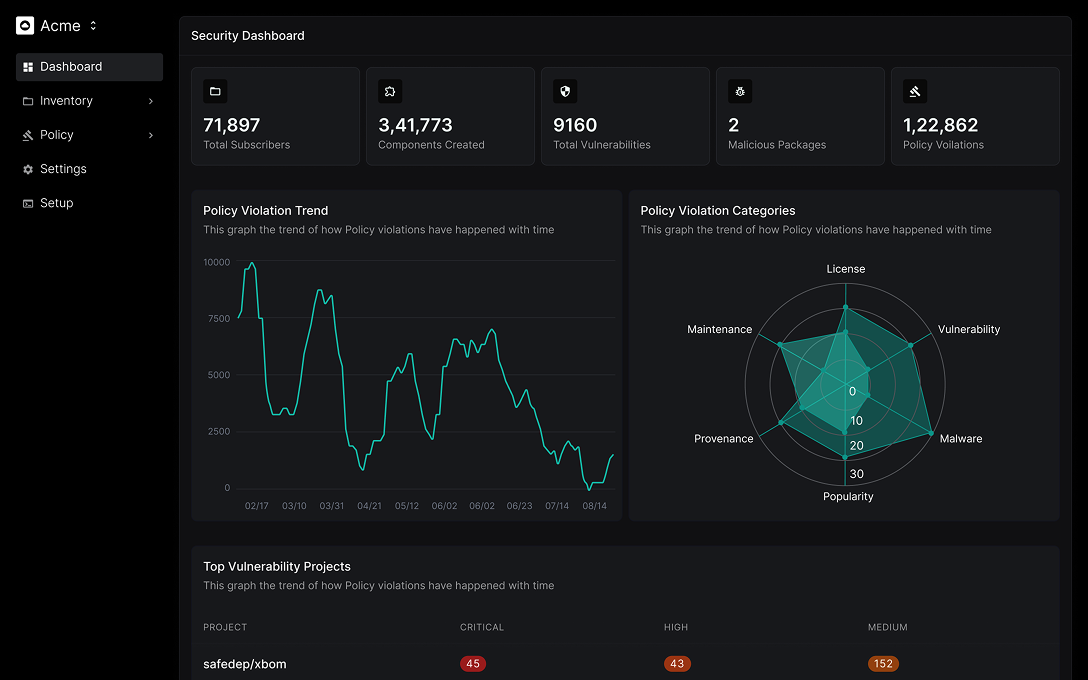
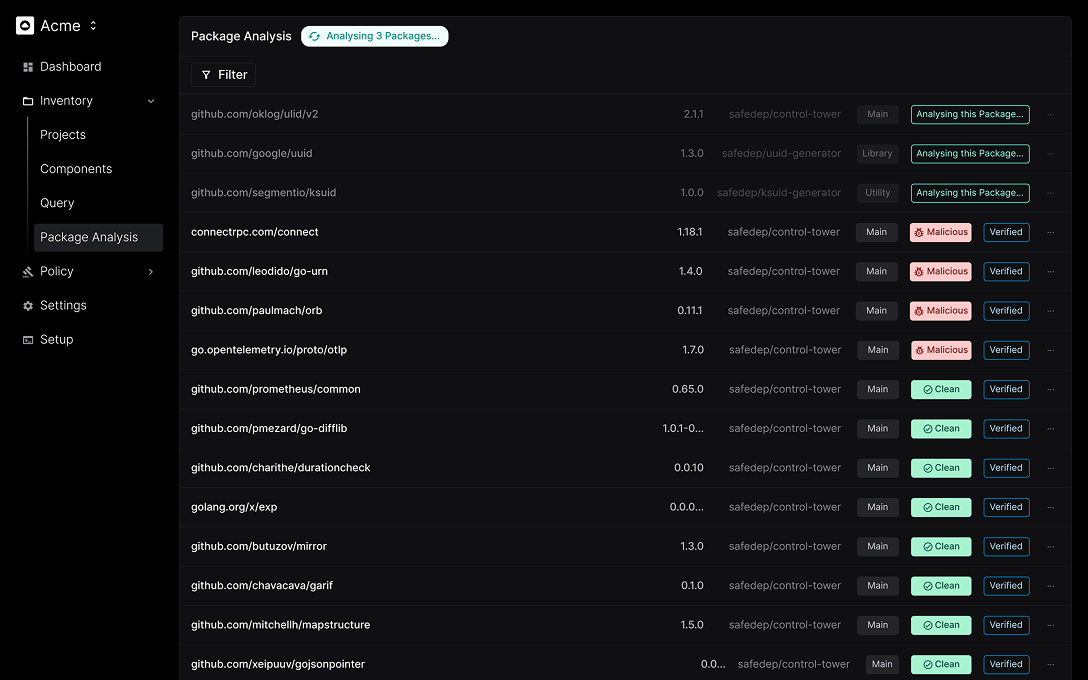
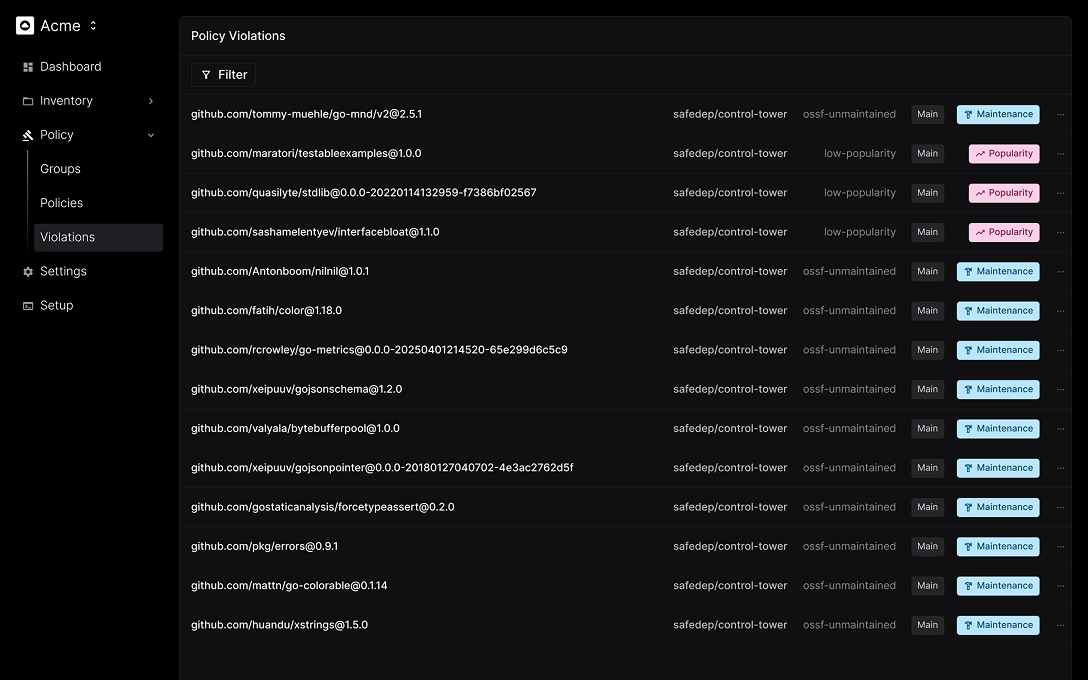
Your Open Source Security Toolkit
Delivers guardrails, visibility, and automation to block malware.
AI and Security Experts Powered Triage
Let SafeDep's AI analyse suspicious packages and prioritise what matters.
Compliance & Audit Reports
Generate SBOMs, license reports, and audit logs on demand.
Full Ecosystem Coverage
Works with npm, PyPI, RubyGems, Go, and more, all from one platform.
Works with Your Stack
Using GitHub Actions, GitLab, or Jenkins? You're covered. We fit right into your pipeline. No extra setup, no new tabs.

Developed for Security
Designed as Open Source
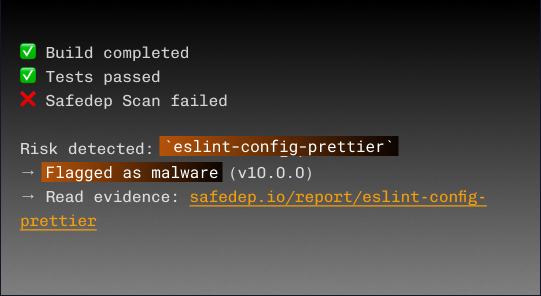
SafeDep VET
You open a pull request.
VET scans the diff. If there's malware, we block the merge, right in your CI.
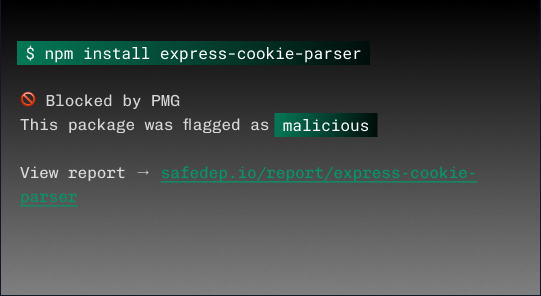
SafeDep PMG
You run NPM Install
PMG checks the package. If it's malware, we block it, right there in your terminal.

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
