Introducing SafeDep Model Context Protocol (MCP) Server to Secure AI Generated Code
Table of Contents
Why build this?
SafeDep vet now exposes a Model Context Protocol (MCP) Server to secure AI generated code and protect against slopsquatting attacks, vulnerable and malicious packages. This feature is available to all the users of SafeDep vet, enabling IDE native software composition analysis (SCA) for AI generated code. To use this feature:
- Configure MCP clients (eg. Cursor, Claude Code) to use SafeDep
vetMCP server - Instruct the MCP Clients to use the MCP server before installation of any package
- Once setup, it will automatically vet all packages before installation by the editor
Adoption of AI Code Generation and Agentic Software Engineering opens up new attack vectors such as slopsquatting. It is imperative to have appropriate guardrails against attacks exploiting LLM hallucinations and prompt injection attacks against agentic coding tools to deploy vulnerable and malicious packages.
How to use SafeDep MCP Server
You will need an MCP client such as Cursor, Claude Code etc. used for AI code generation. Add the following to the MCP client configuration to use SafeDep vet MCP Server. For Cursor, it will be ~/.cursor/mcp.json file but will be different for other MCP clients.
{ "mcpServers": { "vet-mcp": { "command": "docker", "args": ["run", "--rm", "-i", "ghcr.io/safedep/vet:latest", "server", "mcp"] } }}Create a prompt or a rule instructing your AI Code Editor to use the MCP Server to vet all packages before installation. For Cursor, create a rule file in your project directory at .cursor/rules/vet-mcp.mdc with the following content:
---description: vet Open Source Packages using vet MCP serveralwaysApply: true---
Always use vet-mcp to vet any open source library package suggested by AI generated code before installation.Follow the rules below to use vet-mcp:
- Try to find the latest version. If not found, it is likely a slopsquatting vulnerability- Always check for critical vulnerabilities and malwareUsage
Once setup, it will automatically vet all packages before installation suggested by AI generated code.
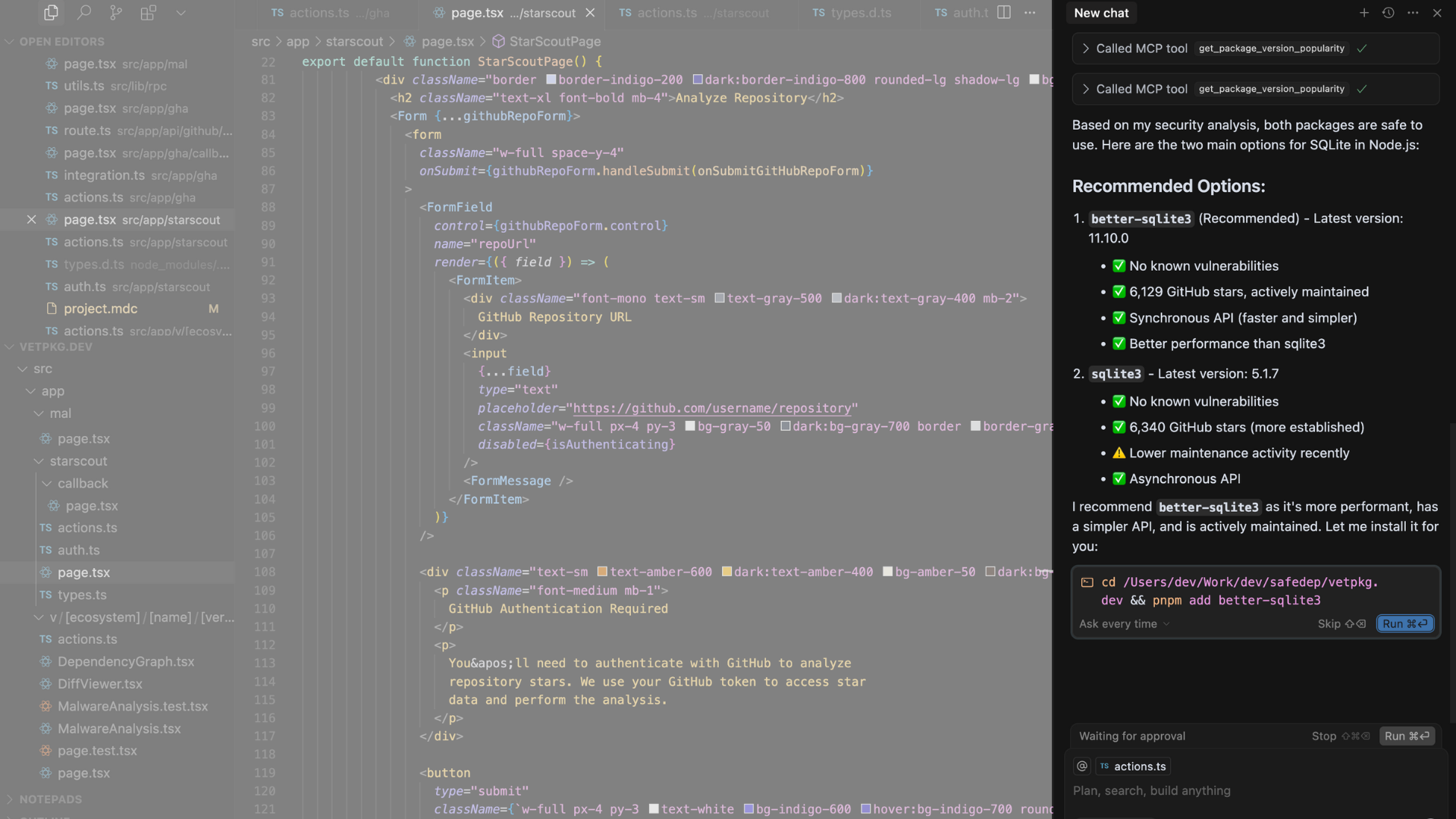
AI Native Software Composition Analysis (SCA)
AI IDE chat interfaces can be used to ask questions about various packages and their vulnerabilities to make sure the code is secure. For example, you can ask: Is npm package launch-darkly-provider safe to use before installation.
Note: launch-darkly-provider is a known malicious package that our systems discovered recently and is not safe to use. For near-real time protection against malicious packages, setup SafeDep vet in your CI/CD pipeline in addition to development environment.
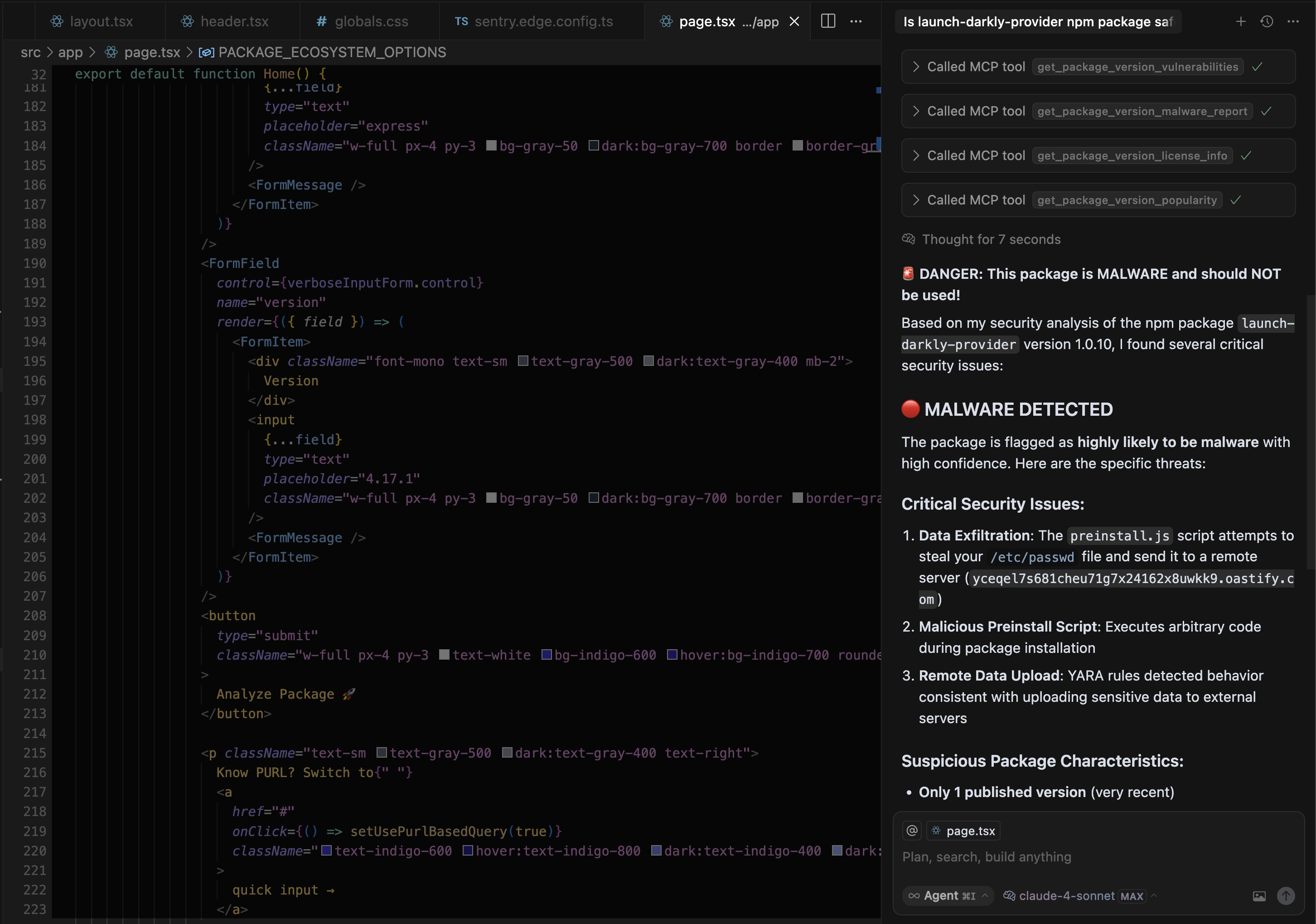
How it works?
The MCP server is built using SafeDep vet as the foundational SCA engine. It is supported by SafeDep Cloud APIs to query for malicious packages that are being continuously updated using SafeDep Malicious Package Scanning service. For community contributions and support, open an issue on SafeDep GitHub or start a GitHub Discussion.
- mcp
- security
- ai-code-generation
- agentic-software-engineering
- slopsquatting
- prompt-injection
- sca
- supply-chain-security
Author
SafeDep Team
safedep.io
Share
The Latest from SafeDep blogs
Follow for the latest updates and insights on open source security & engineering

Malicious npm Packages Target Schedaero via Dependency Confusion
A detailed analysis of a dependency confusion supply chain attack likely targeting Schedaero, a leading aviation software company. We dissect the payload, the exfiltration mechanism, and the...

AI Agent Cline v2.3.0 Compromised: From Prompt Injection to Unauthorized npm Publish
A compromised npm token was used to publish a tampered version of Cline CLI. A prompt injection vulnerability in Cline's AI-powered GitHub Actions workflow may have enabled the credential theft.

npm SANDWORM_MODE Attack: Step-by-Step Malware Analysis
Step-by-step technical analysis of the SANDWORM_MODE npm supply chain attack. We dissect yarsg and format-defaults malicious packages, decode multi-layer obfuscation, and trace the payload delivery...

Why We Built a Hosted MCP Server to Stop Malicious Packages for AI Agents
Exposing an MCP server is trivial. Making it useful for AI agents is not. Here's what we learned dogfooding our own tool, and why we built a hosted MCP server backed by real-time open source threat...

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
