Typosquatt alert ! Malicious npm Package: nyc-config
Table of Contents
Recently, we discovered a malicious npm package nyc-config in our internal Open Source Software (OSS) package monitoring dashboard. It involved sending user system data to external domains. It is a possible typosquatt attack against the widely adopted @istanbuljs/load-nyc-config, which boasts ~25M weekly downloads.
Discovery and Analysis
Our automated malware analysis flagged the nyc-config package as malicious due to System Information Exfiltration. Upon manual inspection, we observed that the package’s package.json file contained a preinstall script designed to execute the index.js file during installation step itself. This script was crafted to gather sensitive system information such as:
- Hostname
- Operating system details
- Local and public IP addresses
- Username
- Current working directory
The collected data was then exfiltrated to remote servers controlled by the attacker.
You can view the analysis here - https://platform.safedep.io/community/malysis/01JP01T1WQPNGAG516NDS9A6ST
Community Engagement
Recognizing the severity of this threat, we promptly reported our findings to the Open Source Security Foundation (OSSF) - https://github.com/ossf/malicious-packages/pull/839
Conclusion
This incident underscores the critical importance of being cautious when incorporating third-party packages, ensuring they originate from trusted sources. By staying vigilant and fostering collaborative efforts, we can collectively mitigate the risks posed by malicious actors and fortify the security of our development environments.
- npm
- malware
- typosquatting
- open-source security
Author
SafeDep Team
safedep.io
Share
The Latest from SafeDep blogs
Follow for the latest updates and insights on open source security & engineering
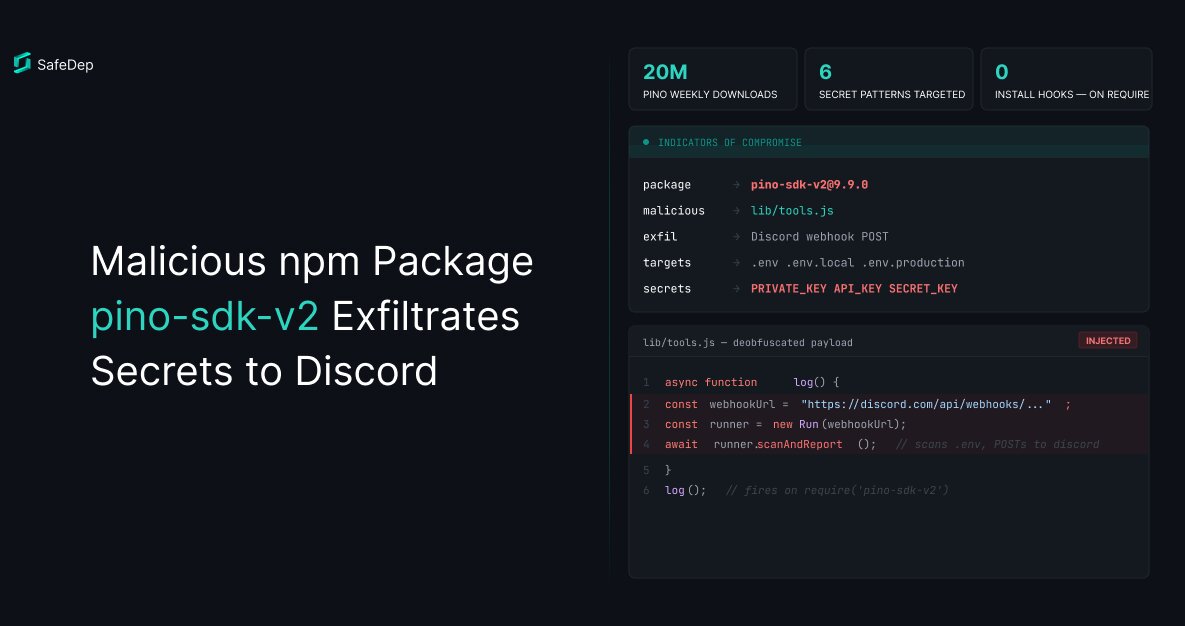
Malicious npm Package pino-sdk-v2 Exfiltrates Secrets to Discord
A malicious npm package impersonating the popular pino logger was detected by SafeDep. The package hides obfuscated code inside a legitimate library file to steal environment secrets and send them to...

Integrate SafeDep MCP in GitHub Agentic Workflow
Learn how to integrate SafeDep MCP with GitHub Agentic Workflows to automatically evaluate the security posture of OSS dependencies in your pull requests using AI.
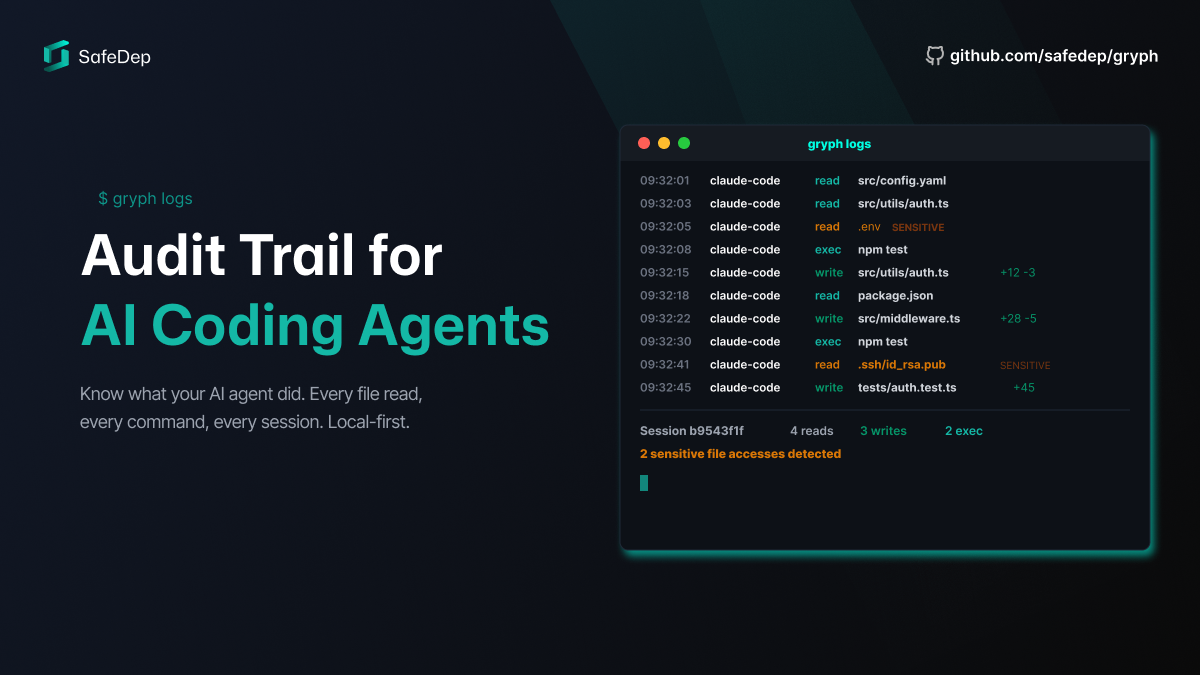
Gryph: Audit Trail for AI Coding Agents
AI coding agents operate with broad access to your codebase, credentials, and shell. Gryph logs every action they take to a local SQLite database, making agent behavior visible, queryable, and...
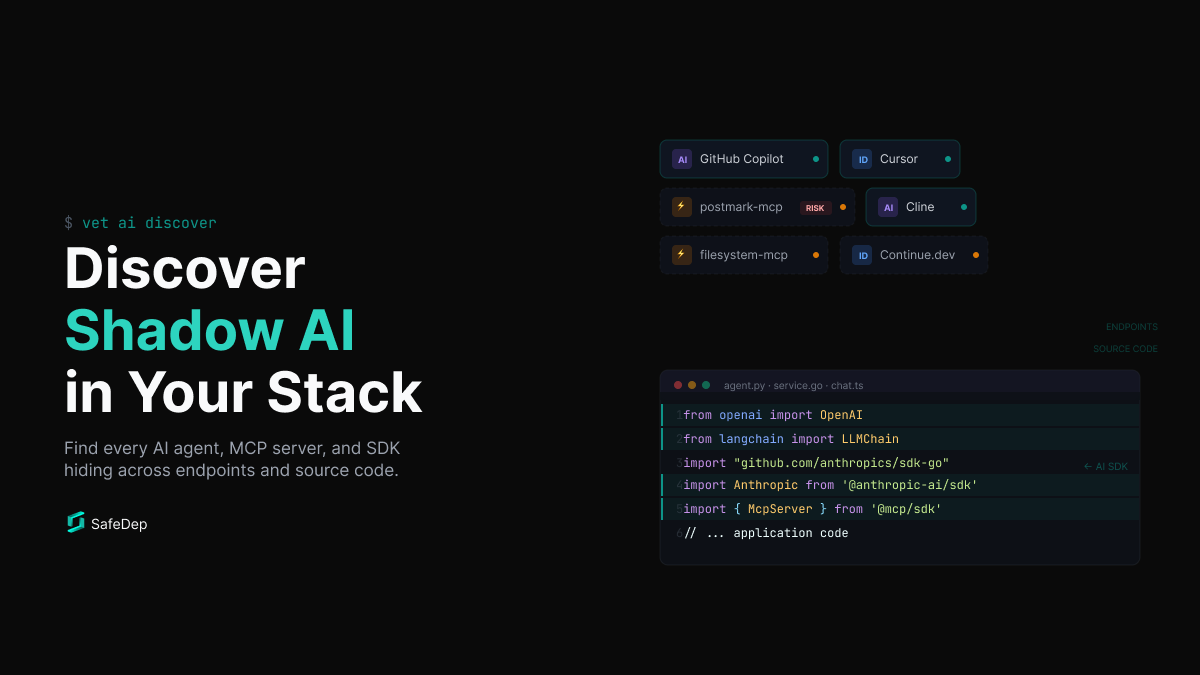
Shadow AI Discovery: Find Every AI Tool and SDK in Your Stack
AI tools and SDKs are spreading across developer environments faster than security teams can track. vet discovers agents, MCP servers, extensions, and AI SDK usage in code. Open source, local, one...

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
