Secure Vibe Coding with AI Agents
Table of Contents
Vibes and More
Recently eslint-config-prettier, an npm package with more than 30 million weekly downloads was compromised. We wrote about it in our earlier blog eslint-prettier-config: Major Supply Chain Attack on npm. But the fact remains, npm like other public open source package registries, is a source of supply chain attack through malicious open source packages published in these registries. AI IDEs and coding agents are likely to accelerate the risk of malicious packages in the software supply chain.
We built SafeDep vet to protect software development teams against malicious packages in CI/CD. But this is not enough when it comes to AI coding agents like OpenAI Codex, Claude Code and AI IDEs like Cursor, Windsurf and others. Lets see with an example.
Vibing like a pro
Consider you are in the vibe of building the world’s best cli tool with an outstanding DevEx. You start with a boilerplate Typescript project that contains only a few dependencies like tsc.
➜ pnpm ls --depth 100 --parseable | wc -l 8You love Claude Code and you start with a prompt like this:
Set the foundation for building a multi-command cli tool withthe best developer experience for cli with interactive,progress bars and other eye candiesClaude Code vibes along with you and comes up with a plan.
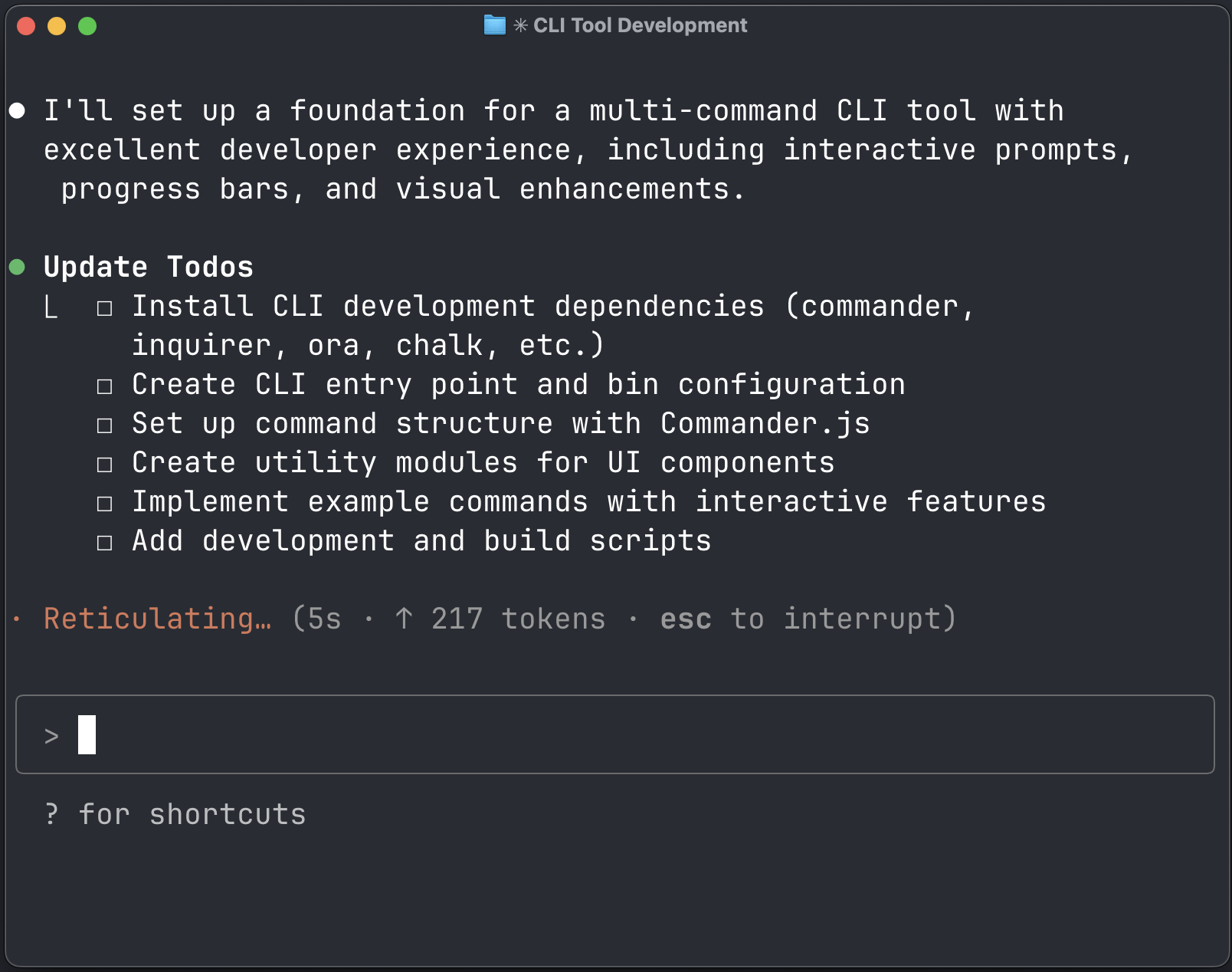
The plan starts with installing a bunch of 3rd party npm libraries. You are in vibe mode and go ahead with installing the 8 libraries that Claude Code suggested.

After this step, you suddenly realize the number of 3rd party dependencies, code from open source, have increased to a staggering 165. You are not sure what these libraries do, but you trust Claude Code to have suggested the best libraries for your cli tool.
➜ pnpm ls --depth 100 --parseable | wc -l 165You are an advanced vet user and you run a quick vet scan to check for potentially unpopular packages.
➜ vet --no-banner scan -M pnpm-lock.yaml \ --insights-v2 --report-summary=false \ --filter 'projects.exists(p, p.stars < 50)'
┌──────────────────────────┬─────────┐│ PACKAGE │ VERSION │├──────────────────────────┼─────────┤│ proto-list │ 1.2.4 ││ util-deprecate │ 1.0.2 ││ widest-line │ 4.0.1 ││ os-tmpdir │ 1.0.2 ││ @pnpm/config.env-replace │ 1.1.0 ││ stubborn-fs │ 1.2.5 ││ run-async │ 3.0.0 ││ is-path-inside │ 4.0.0 ││ @pnpm/network.ca-file │ 1.0.2 ││ @pnpm/npm-conf │ 2.3.1 ││ ansi-align │ 3.0.1 ││ restore-cursor │ 3.1.0 ││ get-east-asian-width │ 1.3.0 ││ is-fullwidth-code-point │ 3.0.0 ││ stdin-discarder │ 0.2.2 ││ is-in-ci │ 1.0.0 ││ cli-width │ 4.1.0 ││ external-editor │ 3.1.0 ││ string_decoder │ 1.3.0 ││ when-exit │ 2.1.4 │└──────────────────────────┴─────────┘You realize that you are not in control of the dependencies you are installing. You are in vibe mode and you are not thinking about the security implications of the dependencies you are installing. Many of the dependencies are not backed by even a modest community and has a similar threat profile as eslint-config-prettier. Then you hear about Slopsquatting and thats when it strikes you. The risk of getting hacked due to malicious code from open sources is real.
Adding a pinch of security
Thats where vet MCP Server comes in. We don’t want to get in the way of your vibe coding adventures but protect you from getting hacked while vibe coding. Lets do this.
Install vet with homebrew or learn more about other installation options.
brew install safedep/tap/vetAdd vet as an MCP server in Claude Code
➜ claude mcp add safedep-vet vet server mcpAdded stdio MCP server safedep-vet with command: vet server mcp to local configAdd the following to your CLAUDE.md file
Always use vet-mcp to check for vulnerabilities and malwarebefore installing any package.Thats it! Lets take Claude Code and vet for a spin.
Install [email protected]Note: pkg:npm/[email protected] is a known malicious package. Here we use it to test vet MCP server integration with Claude Code.
Claude Code now vets all open source packages using vet MCP server, protecting you from getting hacked due to malicious code from open sources.
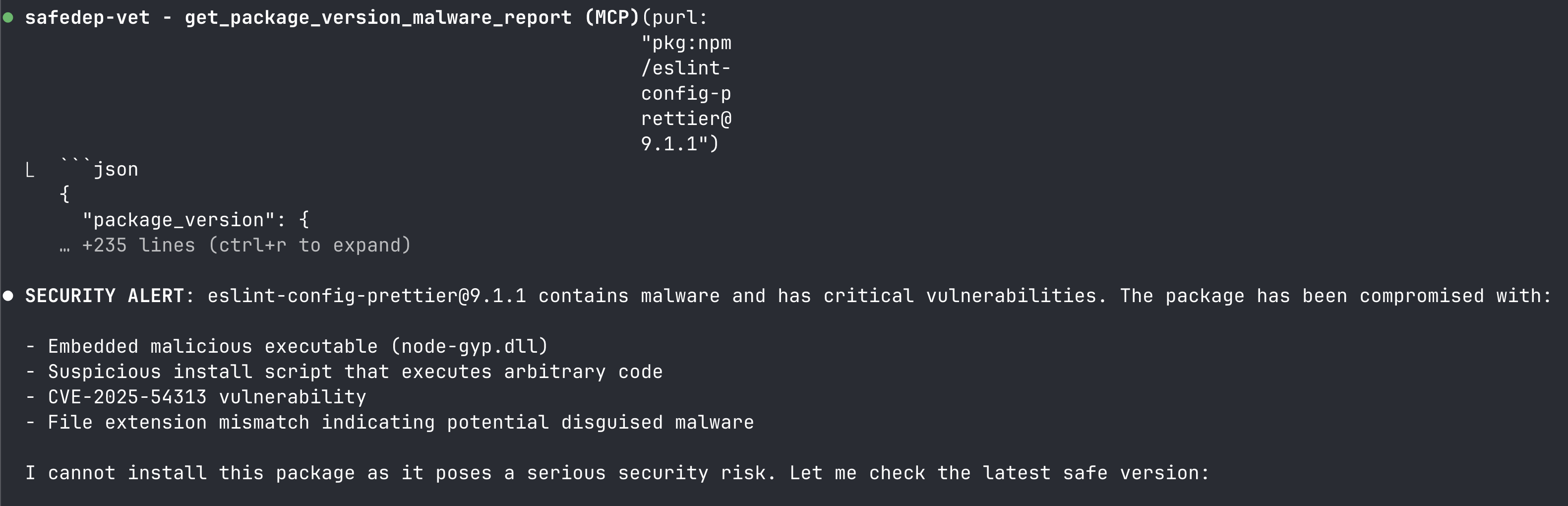
No more getting pwned while vibe coding. You can continue your vibe coding adventures, albeit with a bit of security guardrails in place. vet MCP Server supports all AI IDEs and coding agents that supports MCP. Read the MCP Server Documentation for more details.
Conclusion
While vibe coding is fun, security risks are real. Specifically, ensure that
- Generated code is reviewed before use in production
- Security vulnerabilities in generated code are fixed before use in production
- Open source packages are vetted before installation
Finally, if you are curious, this is how the cli looks like after our vibe coding session.
- npm
- oss
- malware
- vibe-coding
- claude-code
Author
SafeDep Team
safedep.io
Share
The Latest from SafeDep blogs
Follow for the latest updates and insights on open source security & engineering

Malicious npm Packages Target Schedaero via Dependency Confusion
A detailed analysis of a dependency confusion supply chain attack likely targeting Schedaero, a leading aviation software company. We dissect the payload, the exfiltration mechanism, and the...

AI Agent Cline v2.3.0 Compromised: From Prompt Injection to Unauthorized npm Publish
A compromised npm token was used to publish a tampered version of Cline CLI. A prompt injection vulnerability in Cline's AI-powered GitHub Actions workflow may have enabled the credential theft.

npm SANDWORM_MODE Attack: Step-by-Step Malware Analysis
Step-by-step technical analysis of the SANDWORM_MODE npm supply chain attack. We dissect yarsg and format-defaults malicious packages, decode multi-layer obfuscation, and trace the payload delivery...

Why We Built a Hosted MCP Server to Stop Malicious Packages for AI Agents
Exposing an MCP server is trivial. Making it useful for AI agents is not. Here's what we learned dogfooding our own tool, and why we built a hosted MCP server backed by real-time open source threat...

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
