Multiple Malicious Python Packages Targeting Bittensor Crypto Developers
Table of Contents
TL;DR
Multiple malicious Python packages targeting crypto developers and their applications were discovered on PyPI. The packages were used to steal funds by executing a stealthy staking operation. In this specific case, the attackers hooked a legitimate staking function to redirect the funds to their own wallet. The attack leveraged typosquatting to target the popular bittensor package.
Following malicious packages were disclosed by GitLab Vulnerability Research Team:
How SafeDep can protect developers?
SafeDep open source tools especially vet and pmg can help protect developers from malicious packages and other open source software supply chain attacks.
Our automated systems flagged the packages as suspicious due to multiple signals, including identifying the malicious code and intention in typosquatting packages. See example
- Hardcoded destination wallet address
5FjgkuPzAQHax3hXsSkNtue8E7moEYjTgrDDGxBvCzxc1nqR - Forced
transfer_all=Trueindicating operations without user consent
| Malicious Package | SafeDep Analysis | Flagged At |
|---|---|---|
[email protected] | Link | 8/6/2025, 2:53:48 AM |
[email protected] | Link | 8/6/2025, 2:59:52 AM |
[email protected] | Link | 8/6/2025, 3:03:45 AM |
[email protected] | Link | 8/6/2025, 3:16:03 AM |
[email protected] | Link | 8/6/2025, 3:17:10 AM |
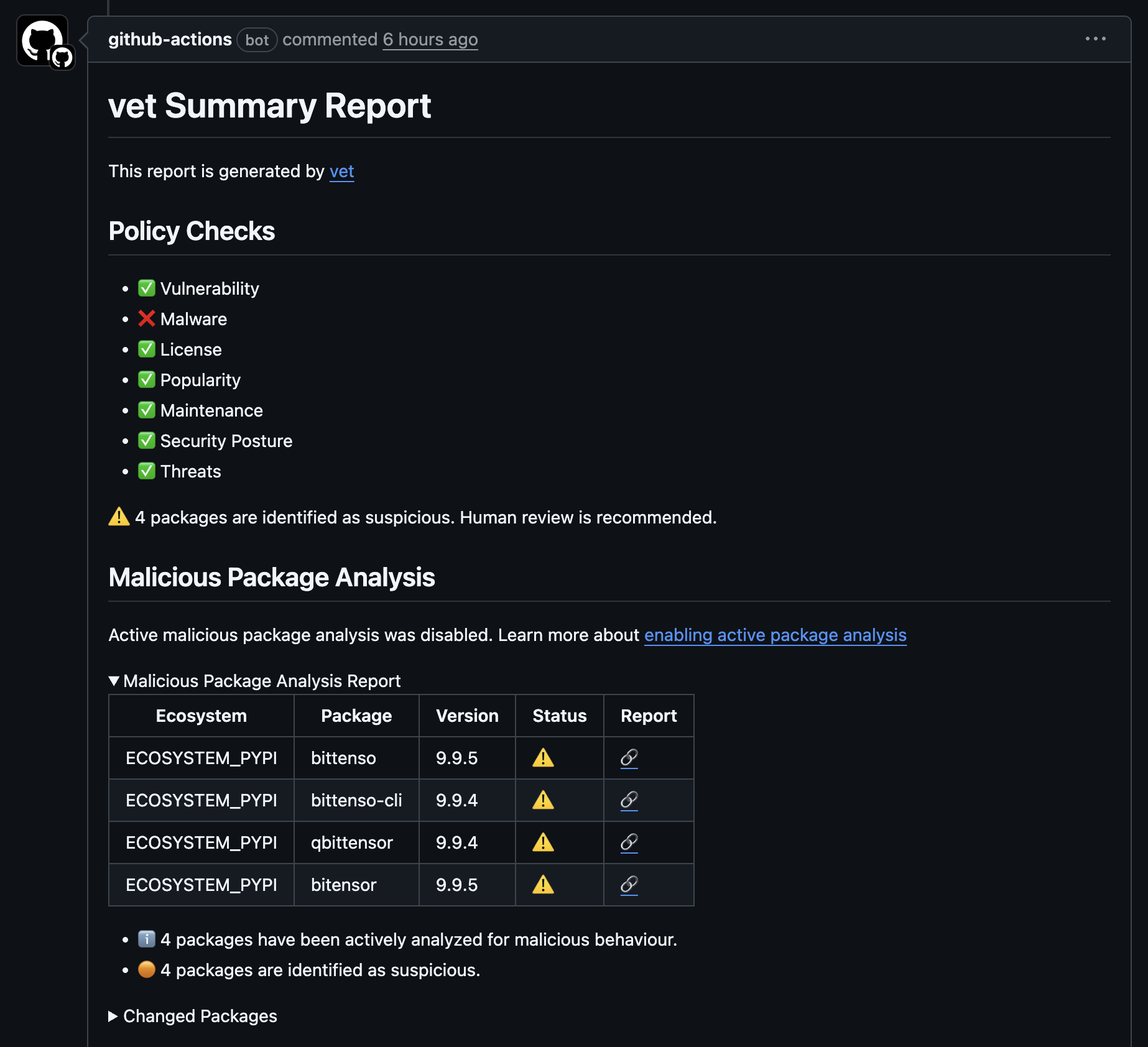
SafeDep vet alerted users in CI/CD pipelines when trying to add any of the compromised package through a PR.
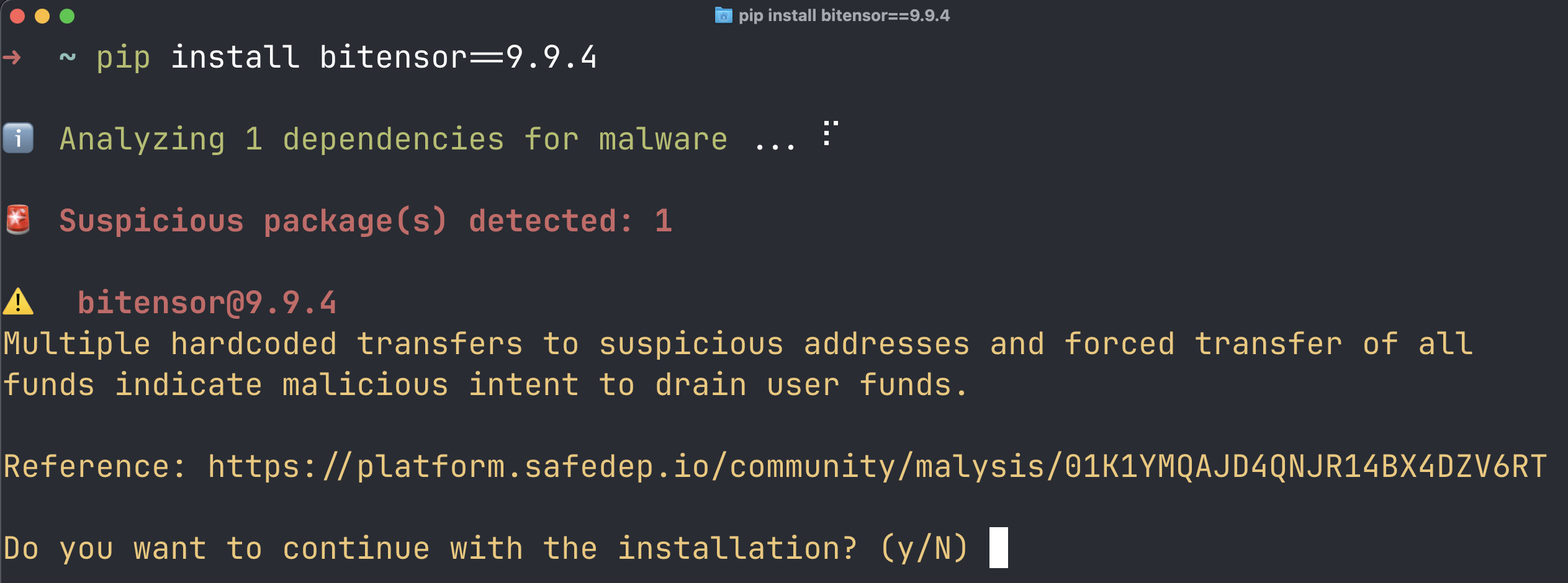
SafeDep pmg will alert developers when trying to install any of the compromised package.
How to protect your project?
At SafeDep, we believe code is the source of truth. We perform code analysis to detect vulnerabilities and malicious code in open source packages. If that is not feasible, general security best practices can be used to protect against common open source software supply chain attacks.
- Always vet open source packages for vulnerabilities and malicious code before use
- Ensure branch protection rules require code review before merging
- Establish trust on packages through its popularity, community or code review
- Avoid using most recently released package versions
- Prefer using open source packages only from trusted sources
SafeDep vet seamlessly integrates with your CI/CD pipeline and alerts you when trying to add any of the compromised package through a PR. SafeDep pmg will alert developers when trying to install any of the compromised package.
References
- pypi
- oss
- malware
- crypto
Author
SafeDep Team
safedep.io
Share
The Latest from SafeDep blogs
Follow for the latest updates and insights on open source security & engineering

npm SANDWORM_MODE Attack: Step-by-Step Malware Analysis
Step-by-step technical analysis of the SANDWORM_MODE npm supply chain attack. We dissect yarsg and format-defaults malicious packages, decode multi-layer obfuscation, and trace the payload delivery...

Why We Built a Hosted MCP Server to Stop Malicious Packages for AI Agents
Exposing an MCP server is trivial. Making it useful for AI agents is not. Here's what we learned dogfooding our own tool, and why we built a hosted MCP server backed by real-time open source threat...

AI Agent Cline v2.3.0 Compromised: From Prompt Injection to Unauthorized npm Publish
A compromised npm token was used to publish a tampered version of Cline CLI. A prompt injection vulnerability in Cline's AI-powered GitHub Actions workflow may have enabled the credential theft.

End-to-End test with Nextjs, Playwright and MSW
A practical Next.js 16 App Router E2E setup with Playwright and MSW that keeps server-side fetch deterministic by focusing mocking where it matters, not on server actions.

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
