AI Agent Cline v2.3.0 Compromised: From Prompt Injection to Unauthorized npm Publish
Table of Contents
TL;DR
On February 17, 2026, a compromised npm token was used to publish an unauthorized version of the popular AI coding tool, [email protected]. The version contained a modified package.json with a postinstall script that silently installed another package globally.
What Happened?
According to the GitHub Security Advisory GHSA-9ppg-jx86-fqw7, an unauthorized party gained access to an npm publish token and released [email protected]. The malicious version was live for roughly 8 hours (3:26 AM to 11:30 AM PT on February 17) before being deprecated.
Security researcher Adnan Khan’s investigation identified a prompt injection vulnerability in Cline’s AI-powered issue triage workflow. The workflow used claude-code-action with broad tool permissions (Bash, Write, Edit) and allowed any GitHub user to trigger it by opening an issue. A crafted issue title could inject a prompt that tricks Claude into running npm install from an attacker-controlled fork. Because the triage workflow shared GitHub Actions cache scope with Cline’s nightly publish workflow, this could be chained with cache poisoning to exfiltrate publication secrets (NPM_RELEASE_TOKEN, VS Code Marketplace, and OpenVSX credentials). The exact method of token theft has not been publicly confirmed. Notably, these tokens were scoped to publisher identity rather than individual extensions, meaning nightly credentials could publish production releases.
What Does the Payload Do?
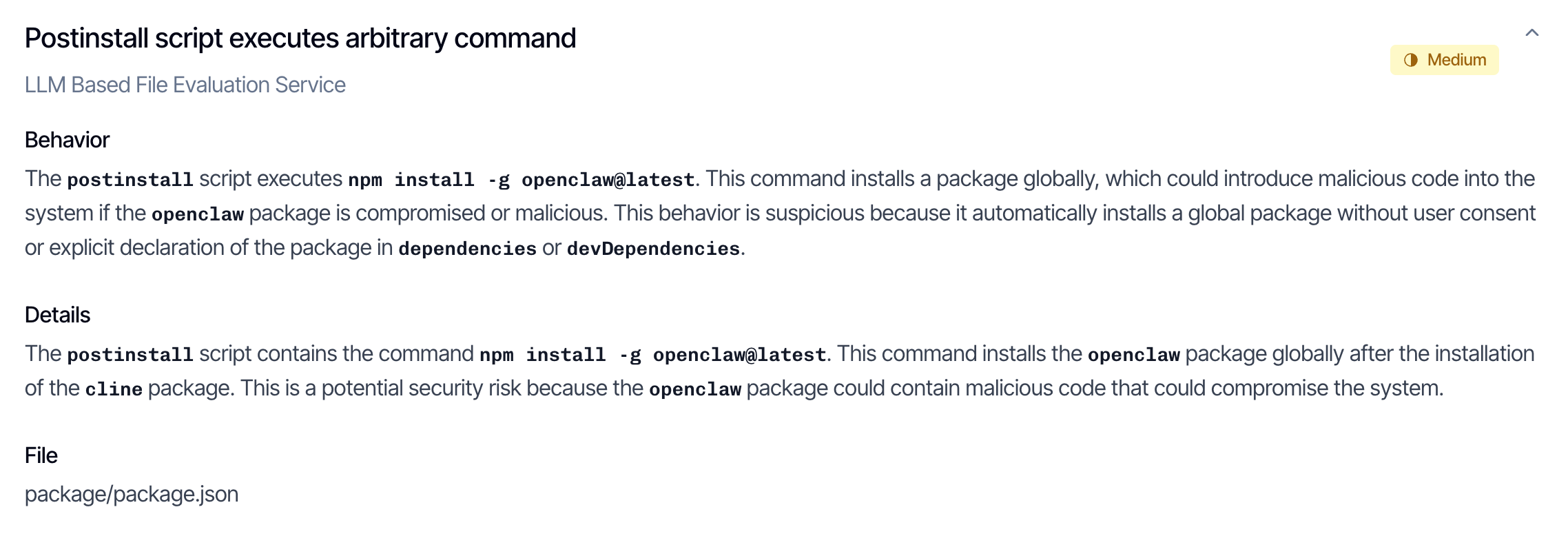
The postinstall script was: "postinstall": "npm install -g openclaw@latest"
OpenClaw is a legitimate, non-malicious open-source project. The payload did not steal credentials, install backdoors, or exfiltrate data. This looks like a proof of concept: someone demonstrating the attack’s feasibility rather than deploying an operational payload. The same postinstall hook could have delivered a credential stealer or reverse shell to every developer who ran npm install -g [email protected]. The mechanism was proven, even if the payload was benign.
The Diff
The only change between the legitimate 2.2.3 (which 2.3.0 was based on) and the compromised version was in the package.json.
Index: package/package.json===================================================================--- package/package.json+++ package/package.json@@ -1,7 +1,7 @@ { "name": "cline",- "version": "2.2.3",+ "version": "2.3.0", "description": "Autonomous coding agent CLI - capable of creating/editing files, running commands, using the browser, and more", "main": "dist/cli.mjs", "bin": { "cline": "./dist/cli.mjs"@@ -31,9 +31,10 @@ "typecheck": "npx tsc --noEmit", "link": "npm run build && npm link", "unlink": "npm unlink -g cline", "test": "vitest",- "test:run": "vitest run"+ "test:run": "vitest run",+ "postinstall": "npm install -g openclaw@latest" }, "keywords": [ "cline", "claude",All other files, including the CLI binary dist/cli.mjs, were identical to the previous version.
How PMG Flagged It
SafeDep Package Manager Guard (PMG) flagged [email protected] as suspicious during installation:
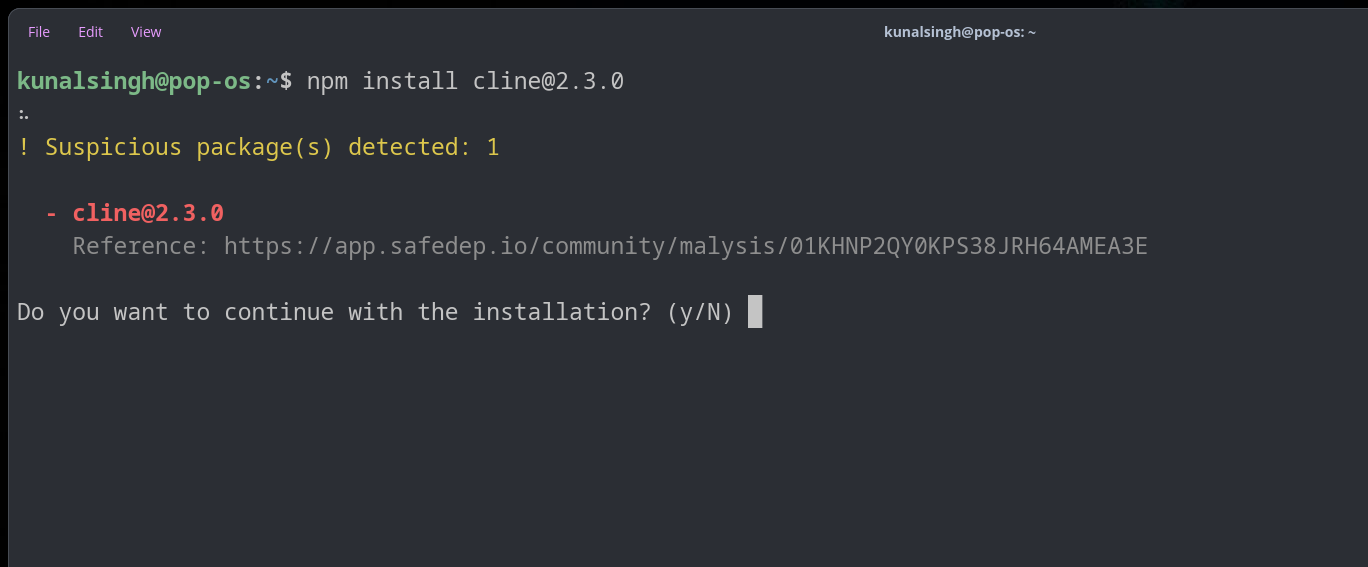
SafeDep’s LLM-based file evaluation identified the postinstall script as executing an arbitrary command, installing a global package without user consent or explicit declaration in dependencies:
Users of pmg would have been blocked or alerted during the attempted installation, preventing the payload from executing.
For teams looking to catch malicious dependencies earlier in the development lifecycle, the SafeDep GitHub App can flag pull requests that introduce known malicious packages before they reach installation.
Post-Incident Response
Cline revoked the compromised token, removed the vulnerable AI triage workflow (PR #9211), and moved npm publishing to OIDC provenance via GitHub Actions. This eliminates long-lived static tokens as an attack surface for future publishes.
Next Steps for Users
If you installed [email protected] between 3:26 AM PT and 11:30 AM PT on February 17:
- Update:
npm install -g cline@latest(version2.4.0or higher) - Cleanup: Remove
openclawif you didn’t intend to install it:npm uninstall -g openclaw
References
- npm
- oss
- malware
- cline
- supply-chain
- prompt-injection
Author
Kunal Singh
safedep.io
Share
The Latest from SafeDep blogs
Follow for the latest updates and insights on open source security & engineering

Why We Built a Hosted MCP Server to Stop Malicious Packages for AI Agents
Exposing an MCP server is trivial. Making it useful for AI agents is not. Here's what we learned dogfooding our own tool, and why we built a hosted MCP server backed by real-time open source threat...

Agent Skills Threat Model
Discover critical security threats in Agent Skills - Anthropic's open format for AI agent capabilities. Learn about supply chain attacks, deferred code execution, prompt injection, and multiple...

End-to-End test with Nextjs, Playwright and MSW
A practical Next.js 16 App Router E2E setup with Playwright and MSW that keeps server-side fetch deterministic by focusing mocking where it matters, not on server actions.

The State of MCP Registries
Explore the architecture of the Model Context Protocol (MCP) and the state of its official registry. Learn how to consume server packages programmatically and discover the underlying challenges of...

Ship Code
Not Malware
Install the SafeDep GitHub App to keep malicious packages out of your repos.
